Overview
At Safe-T, we have one goal; to keep your organization safe from attacks and data leakage by securing your access. Enabling secure application and file access is our company’s passion and purpose, driving everything we do as an organization.
Comprised of industry leaders from B2B security firms and government agencies as well as elite military units, we understand and appreciate the complex challenges of protecting data in the Digital Transformation. Today, securing sensitive data is more difficult—and more important —than ever before. Modern scanning and hacking tools mean that attackers have their sights set on every organization, regardless of size or vertical. This makes you a target. We are here to help you take control your access for applications and files, two of the most common corporate entry points for malware and other threats.
There is a lot of talk about Zero Trust in the security world today. Far from just jumping on the ZT bandwagon, ensuring completely secure access to files and applications is a key element of establishing a robust and resilient security strategy. But that secure access needs to be user-friendly, to help employees get to the resources they need quickly, without hassle. Our unique approach gives IT teams and security leaders the locked-down access they need while streamlining procedures for employees to make it simple and frustration-free.
Providing our users with these two seemingly opposing feature sets is a tall order but it is exactly what we do here, every day, for every customer. This is why we are proud to call ourselves the Masters of Access.
Comprised of industry leaders from B2B security firms and government agencies as well as elite military units, we understand and appreciate the complex challenges of protecting data in the Digital Transformation. Today, securing sensitive data is more difficult—and more important —than ever before. Modern scanning and hacking tools mean that attackers have their sights set on every organization, regardless of size or vertical. This makes you a target. We are here to help you take control your access for applications and files, two of the most common corporate entry points for malware and other threats.
There is a lot of talk about Zero Trust in the security world today. Far from just jumping on the ZT bandwagon, ensuring completely secure access to files and applications is a key element of establishing a robust and resilient security strategy. But that secure access needs to be user-friendly, to help employees get to the resources they need quickly, without hassle. Our unique approach gives IT teams and security leaders the locked-down access they need while streamlining procedures for employees to make it simple and frustration-free.
Providing our users with these two seemingly opposing feature sets is a tall order but it is exactly what we do here, every day, for every customer. This is why we are proud to call ourselves the Masters of Access.
The Dangers of Exposed Applications
As organizations continue to “go digital” and become more connected, they open their networks and internal applications to remote employees, customers, business partners, 3rd party vendors, mobile devices, and connected devices.
Enhanced connectivity is necessary to remain business-relevant, but it comes at a cost; Research shows that six out of ten organizations around the globe have suffered at least one cyber-attack on their enterprise services.
This shouldn’t be the case in our technologically sophisticated world. But it is, because organizations typically expose their services to the internet in order to interact with their many 3rd party vendors and external partners. The fact is that organizations are still using legacy methods such as VPN and virtual desktop solutions of designing perimeter networks that don’t account for modern connectivity and application access challenges.
It is clear that organizations need a paradigm shift to overcome the challenges of providing simple, cost effective, and transparent access to internet facing services, while effectively combatting cyber-attacks and threats.
Enhanced connectivity is necessary to remain business-relevant, but it comes at a cost; Research shows that six out of ten organizations around the globe have suffered at least one cyber-attack on their enterprise services.
This shouldn’t be the case in our technologically sophisticated world. But it is, because organizations typically expose their services to the internet in order to interact with their many 3rd party vendors and external partners. The fact is that organizations are still using legacy methods such as VPN and virtual desktop solutions of designing perimeter networks that don’t account for modern connectivity and application access challenges.
It is clear that organizations need a paradigm shift to overcome the challenges of providing simple, cost effective, and transparent access to internet facing services, while effectively combatting cyber-attacks and threats.
Introducing Safe-T ZoneZero® SDP
Safe-T’s Zero Trust Network Access (ZTNA) solution, ZoneZero® SDP, is changing the way organizations grant secure external access to their services.
ZoneZero® SDP offers secure and transparent access for all types of entities (people, applications, and connected devices) to any internal application, service, and data, for example HTTP/S, SMTP, SFTP, SSH, APIs, RDP, and WebDAV.
ZoneZero® SDP implements Safe-T’s patented reverse-access (outbound) technology which eliminates the need to open incoming ports in the organization’s firewall. The solution forces users to authenticate into resources first and then they are granted access by the solution. Configurable policies define the orchestrated authentication steps that each user or group member must perform.
Now, backend services are not visible to unauthenticated users and the probability of suffering
a successful attack is minimized. It’s like we always say here at Safe-T: Zero Trust – The Right Way®
ZoneZero® SDP offers secure and transparent access for all types of entities (people, applications, and connected devices) to any internal application, service, and data, for example HTTP/S, SMTP, SFTP, SSH, APIs, RDP, and WebDAV.
ZoneZero® SDP implements Safe-T’s patented reverse-access (outbound) technology which eliminates the need to open incoming ports in the organization’s firewall. The solution forces users to authenticate into resources first and then they are granted access by the solution. Configurable policies define the orchestrated authentication steps that each user or group member must perform.
Now, backend services are not visible to unauthenticated users and the probability of suffering
a successful attack is minimized. It’s like we always say here at Safe-T: Zero Trust – The Right Way®
Safe-T’s Reverse Access Technology
Safe-T’s Reverse-Access* is a dual server patented technology, which removes the need to open any ports within a firewall while allowing secure application access between networks (through the firewall).
- External node – installed in the DMZ/external/non-secured segment.
- Internal node – installed in the internal/secured segment.
Located in the organization’s DMZ (on-premises or cloud), the role of the external node is to act as a front-end to all services/applications published to the Internet. It operates without the need to open any ports within the internal firewall therefor ensuring that only legitimate session data can pass through into the internal network. In addition, the external server performs TCP offloading, allowing it to support any TCP based application without the need to perform SSL decryption.
The role of the internal server it to pull the session data into the internal network from the external gateway node, and only if the session is legitimate, pass it to the destination application server. Benefits of our Reverse-Access technology include:
The role of the internal server it to pull the session data into the internal network from the external gateway node, and only if the session is legitimate, pass it to the destination application server. Benefits of our Reverse-Access technology include:
- Access to applications/networks without opening an incoming hole in the firewall.
- Support any TCP based application.
- Bi-directional traffic is handled on outbound connections from the LAN to the outside world.
- Client-less and VPN-less application access.
- Logically segment networks.
Proof of Concept Use Case
With dramatically enhancing the organization’s security posture and eliminating the public attack surface in mind, the customer wishes to provide remote access to critical and sensitive internal applications such as web and RDP services.
Utilizing Safe-T’s ZoneZero® SDP (Software-Defined Perimeter) architecture with its patented Reverse Access technology, remote access is to be provided without the need for open inbound access (no active listeners) over the Internet and without the need for any inbound open firewall ports between the DMZ environment and the internal network.
Remote users wishing to get access to an application or resource would browse using a standard web-browser to Safe-T’s Authentication Gateway which will be publicly accessible over the Internet and deployed at an isolated off-premises location (such as a DMZ or public cloud instance). Following a successful authentication using either Active Directory, a local user repository or a known Identity provider (such as Okta or Duo), users will be granted access to directly connect to the organization and consume the desired application or service over the public Internet and without requiring any agents or clients.
Access to applications will be offered in a native way, using native clients (such as a web browser, standard RDP clients, SQL client, etc.) without affecting the user experience.
Utilizing Safe-T’s ZoneZero® SDP (Software-Defined Perimeter) architecture with its patented Reverse Access technology, remote access is to be provided without the need for open inbound access (no active listeners) over the Internet and without the need for any inbound open firewall ports between the DMZ environment and the internal network.
Remote users wishing to get access to an application or resource would browse using a standard web-browser to Safe-T’s Authentication Gateway which will be publicly accessible over the Internet and deployed at an isolated off-premises location (such as a DMZ or public cloud instance). Following a successful authentication using either Active Directory, a local user repository or a known Identity provider (such as Okta or Duo), users will be granted access to directly connect to the organization and consume the desired application or service over the public Internet and without requiring any agents or clients.
Access to applications will be offered in a native way, using native clients (such as a web browser, standard RDP clients, SQL client, etc.) without affecting the user experience.
Solution Needs example
There was a need to deploy a remote access solution which addresses the following requirements:
- Allow end-users to access to corporate resources without installing a VPN client
- The solution had to support various corporate applications – financing systems, RDP servers, SSH machines, file servers, legacy systems, web applications, etc
- Solution had to be easy for end-users to learn and use
- Solution had to maintain highest levels of security
- Solution had to be deployed quickly at company location
- Solution had to support any size customer and scale easily
Solution Use Cases example
- “Customer name” wishes to publish the below services: o HTTPS – service name, o RDP – service name, o SSH – service name
- “Customer name” wishes to integrate the below services: o Local Active Directory, o FA name (support by REST API / SAML 2.0/ OAuth 2.0), o Syslog
Solution Architecture example
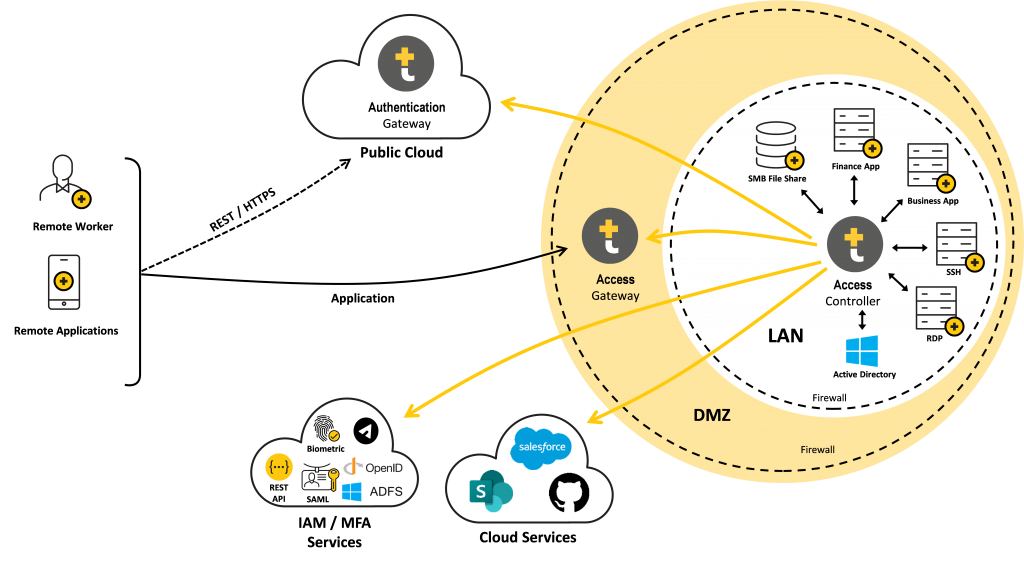
- Safe-T ZoneZero® Authentication Gateway is deployed in a DMZ/cloud customer environment, isolated from other networks, applications, services, or data.
- Safe-T ZoneZero® Access Gateway is deployed in a DMZ/cloud customer environment, isolated from other networks, applications, services, or data.
- Safe-T ZoneZero® Access Controller is deployed on the backend of the network, behind a closed-at-all-times firewall, and in a network segment routable to destination applications.
Detailed Process Flow example
The following describes the process flow of an access request while the service is unpublished to world (no active listeners, service inaccessible):
1. A user requires access to a destination on-premises service or application.
2. The user opens a web browser and types in a URL for the Safe-T ZoneZero® Authentication Gateway (such as https://auth.company.com).
3. The user inputs Active Directory authentication credentials to the web portal.
4. The on-premises Safe-T ZoneZero® Access Controller creates an outbound connection to the Safe-T ZoneZero® Authentication Gateway and pulls the user input into the private network environment (no access is provided at this point).
5. The Safe-T ZoneZero® Access Controller authenticates the user internally by connecting to the local Active Directory service.
6. Once the user is authenticated, Safe-T ZoneZero® Access Controller instructs the DMZ/cloud based Safe-T ZoneZero® Access Gateway (on an outbound connection) to open a port to accept traffic from the user’s unique IP address to be routed to the backend service or application.
7. The user is presented with a web portal containing a list of now-accessible applications. The user clicks on the desired application link to be opened in a web browser, or switches to native client to seamlessly connect for other protocols (such as RDP service).
8. The ZoneZero® Access Controller pulls (on an outbound connection) the user traffic from the Safe-T ZoneZero® Access Gateway and sends it to the destination application. The response is pushed back to ZoneZero® Access Gateway and relayed the user in a seamless way.
9. The user connection is established while the service remains inaccessible and hidden to other users.
1. A user requires access to a destination on-premises service or application.
2. The user opens a web browser and types in a URL for the Safe-T ZoneZero® Authentication Gateway (such as https://auth.company.com).
3. The user inputs Active Directory authentication credentials to the web portal.
4. The on-premises Safe-T ZoneZero® Access Controller creates an outbound connection to the Safe-T ZoneZero® Authentication Gateway and pulls the user input into the private network environment (no access is provided at this point).
5. The Safe-T ZoneZero® Access Controller authenticates the user internally by connecting to the local Active Directory service.
6. Once the user is authenticated, Safe-T ZoneZero® Access Controller instructs the DMZ/cloud based Safe-T ZoneZero® Access Gateway (on an outbound connection) to open a port to accept traffic from the user’s unique IP address to be routed to the backend service or application.
7. The user is presented with a web portal containing a list of now-accessible applications. The user clicks on the desired application link to be opened in a web browser, or switches to native client to seamlessly connect for other protocols (such as RDP service).
8. The ZoneZero® Access Controller pulls (on an outbound connection) the user traffic from the Safe-T ZoneZero® Access Gateway and sends it to the destination application. The response is pushed back to ZoneZero® Access Gateway and relayed the user in a seamless way.
9. The user connection is established while the service remains inaccessible and hidden to other users.
User Experience Flow example
1. A user requires access to a destination on-premises service or application.
2. The user opens a web browser and types in a URL for the Safe-T ZoneZero® Authentication Gateway (such as https://auth.company.com).
3. The user inputs Active Directory authentication credentials to the web portal.
4. The user is presented with a web portal containing a list of now-accessible applications. The user clicks on the desired application link to be opened in a web browser, or switches to native client to seamlessly connect for other protocols (such as RDP service).
5. The user connection is established while the service remains inaccessible and hidden to other users.
2. The user opens a web browser and types in a URL for the Safe-T ZoneZero® Authentication Gateway (such as https://auth.company.com).
3. The user inputs Active Directory authentication credentials to the web portal.
4. The user is presented with a web portal containing a list of now-accessible applications. The user clicks on the desired application link to be opened in a web browser, or switches to native client to seamlessly connect for other protocols (such as RDP service).
5. The user connection is established while the service remains inaccessible and hidden to other users.

